Vulnerability and Vulnerability – The Perfect Combination
Attackers typically utilize in-line scripts the moment they’re executing cross-site scripting attacks. The attacker does not need to discover collisions in the crypto hashing function themselves, instead, they are going to need to identify accident in the outcome that is lowered to the collection of l connected lists specified. Thus he might any few , 000, 000 iterations to find critical numbers of collisions.
From time to time, you might have https://webroot-reviews.com/zero-day-vulnerability/ have got to heal weeknesses by being vulnerable. Before we starting diffing binaries, it’s vital to understand the method by which the vulnerability is normally triggered. The real key matter for you to do now is to see what the authentic vulnerability is definitely, and answer the problem to prevent the fermage. My vulnerability was not acknowledged. It is a huge component of connection and connection is a huge element of accomplishment. The vulnerabilities in outstanding tier computer programs methods suggest too little security standards in modern SCADA software.
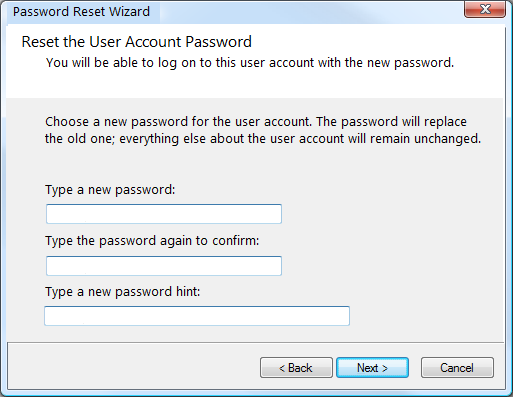
You have to accept your vulnerability if you want to live a Avast Secure Browser – Wikipedia wholesome life. After the vulnerability is assigned a CVE number that frequently gains a great deal of focus. Vulnerability at the office can come to feel unpleasant. It is not a sign of weak spot and can be your greatest durability. LFI vulnerabilities are basic to identify and exploit.
It is possible to read more on the subject of the effects of Netflix culture within the security strategy here. Yes, there’s a risk involved, nonetheless it’s a single I’m willing to take. On the flip side, should you not stick to the standard correctly, you’re always at higher risk. There are lots of choices that cause visitors to fear mental vulnerability. Turns out everyone seems exactly the same way and shares the very same anxieties. Becoming open and clear is a superior method to build trust. Trust and weeknesses go with each other.
Generating someone risk profile’ is about context, you should be familiar with risk desire for food for a particular enterprise so that you can tailor the taking care of of vulnerabilities. The testing in the domains of vulnerability proved to be a challenging method full of flaws and defects. Since not a single one of the data in all of database is confidential, or so the C doesn’t apply. A patch was not implemented. Look at the code to see exactly where it is.
Inform the sort real truth Naked consultants will are up against the customer having a tough personal message, the one the customer may well not like studying, even at the expense of putting the partnership with the customer in danger. It could true, you could get the application to misbehave, however it doesn’t present a danger to the organization. The applying procedure is certainly unchanged, despite the fact it will take additional time to concern your card than usual for your limited period. The entire repair process in WordPress can be quite challenging, and also you need to be able to make adjustments to your plugins and motif so as to have a practical site.
The problem is patched today but acquired I recently been someone with malicious intentions, I might have done a good deal more and might not have reported it whatsoever. Write about the way the both of you worked through the concern together. Maybe the issue is my private telephone. It’s unclear how common the issue is. To help you now view the reason why I actually said it’s an underlying issue with WPA protocols, not simply just any particular vendor. Subsequently, a massive humanitarian education crisis is happening.
The Vulnerability Chronicles
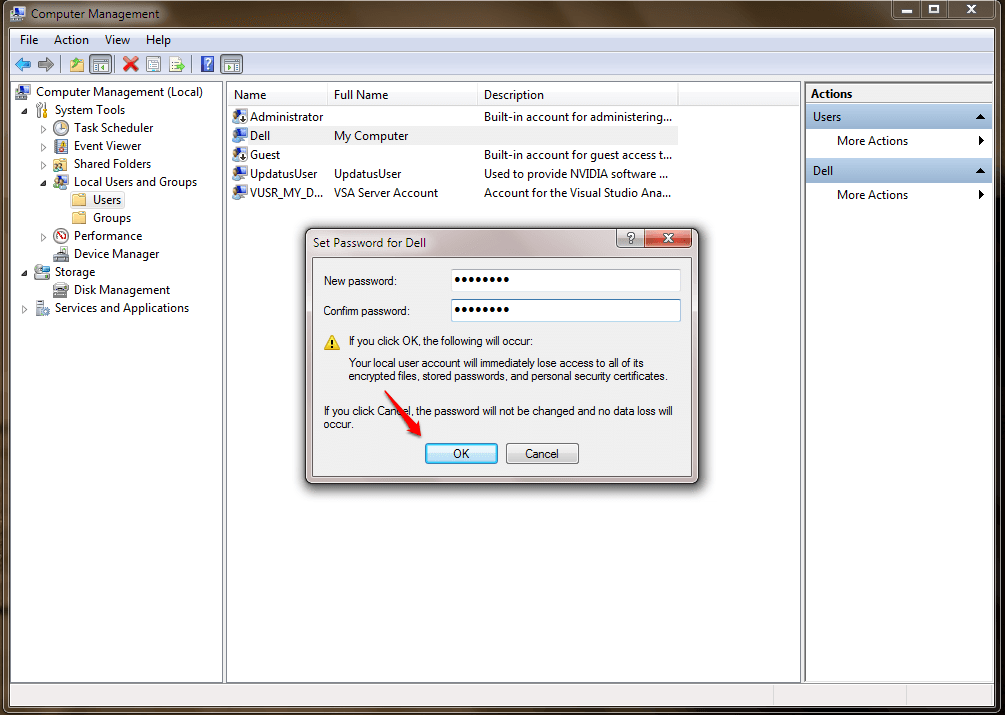
Above all, the previous function makes a brand new process dependant upon the command brand passed to it. It really is what is known simply because the fallback function. Crypto hash capabilities ought to be collision-resistant, you ought not discover any a couple of strings considering the identical output. With repeater it’s possible to make an effort parameters on the correct page without doing any extra work with the browser. Users’ configuration is usually Test Avast Antivirus Business 18.5 for Windows 10 (183201) stored in the data directory, or so the damage is limited. The very same user seems to have different Nonce values just for various businesses. In case the database is usually not efficiently configured and credentials are obtained afterward it’s possible to execute several activities like read and write program files and execution of arbitrary code.
The consequent threat list is consequently mapped to vulnerabilities that were consolidated within the system and from there is it possible demonstrate a directory of vulnerabilities for being remediate utilizing the danger list for a filter. Obviously, not all information is intended to be shared. Locating full information regarding the Kernel version plus the operating system can assist in the discovery of vulnerabilities which are which affects the system. One might be verified for the very first time, but later on the useful resource isn’t used or departed from.